
-
 Rashmi Chiluka
Rashmi Chiluka
-
 396 Views
396 Views
-
 6 Min Read
6 Min Read
-
 3 years ago
3 years ago
In recent years, the cost of data breaches has steadily risen the additional vulnerabilities that occur due to the move to a remote workforce dramatically enhanced the chances for cyber-attacks and introduce several weak points for hackers to exploit. Additionally Automated hacking assaults and the capacity to exchange bitcoin by a ransomware has increased the number of cyber-crimes in general.
2022 has brought with it a slew of new problems for both businesses and both consumers in the midst of a worldwide epidemic forest fires and political instability it’s easy to overlook a serious orbitless physical threat it set a record for data loss due to cyber-attacks and we are yet to see the true crux of this digital revolution.
In situations like these, penetration testing has been a gift to organizations worldwide.
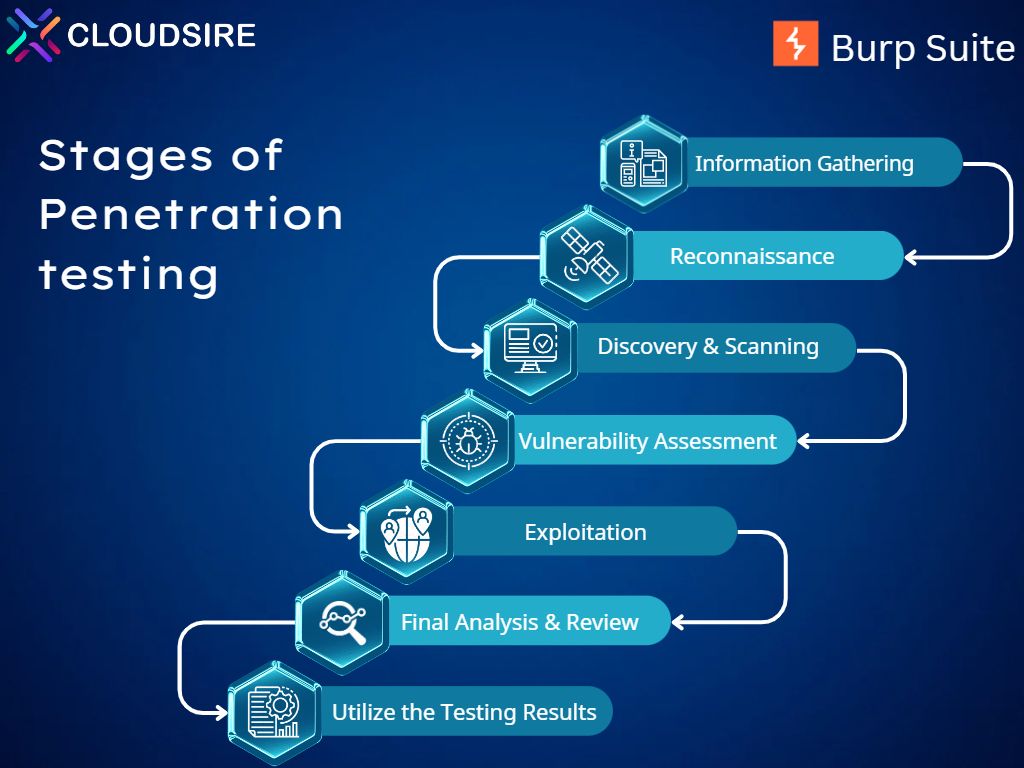
Penetration testing is a simulated attack on websites, mobile apps, sites, or other computer networks in order to find potential vulnerabilities in the network and assess the system's security. Pen testing is broken down into seven stages.
- Information Gathering
- Reconnaissance
- Discovery and Scanning
- Vulnerability Assessment
- Exploitation
- Final Analysis and Review
- Utilize the Testing Results
This article deals with one of the pen testing tools that are used by communities across vastly. One of the best security suites for ethical hacking and pen testing is Burp Suite.
Burp Suite is a comprehensive set of tools for web application security testing and is developed by the company called Portswigger. Dafydd Stuttard had written the first version of Burp. It is one of the best security suites for ethical hacking and pen testing and has several tools required for every phase of testing and analysis that include Burp Proxy, Sock, Spider, Intruder, Comparer, Extender, and Repeater etc, which allow for rapid and versatile testing of web applications.
The Burp Suite for developers is available in two editions. The tools required and necessary for scanning operations are included in the free version. Although the professional and enterprise editions are for sale, you can download and use the community edition for nothing straight from Kali Linux. If advanced version of penetration testing is required, the second edition can be opted. Tools are available to analyse requests made between a browser and destination servers as well as to map the attack surface. The bulk of information security specialists use the framework, which employs Web Penetration Testing on the Java platform.
Burp Suite contains a wealth of features and capabilities to support manual and automated security testing.
Burp Suite comes with a number of tools for carrying out various testing activities. The tools function well together, and as your work advances, you may send interesting requests between tools to complete various tasks. A few important features of burp are:
- Target - This tool contains detailed information about your target applications, and lets you drive the process of testing for vulnerabilities
- Burp's browser - This browser is preconfigured to work with the full functionality of Burp Suite right out of the box.
- Proxy - This is an intercepting web proxy that operates as a man-in-the-middle between the end browser and the target web application. It lets you intercept, inspect and modify the raw traffic passing in both directions.
- Scanner Professional - This is an advanced web vulnerability scanner, which can automatically crawl content and audit for numerous types of vulnerabilities.
- Intruder - This is a powerful tool for carrying out automated customized attacks against web applications. It is highly configurable and can be used to perform a wide range of tasks to make your testing faster and more effective.
WORKFLOW
Stage 1: Map the target application
Burp works in 3 stages. The first one being to map the target application. Mapping out the network structure and the topology takes place once the target names and IP addresses are accessible. Understanding how various networks are interconnected and what kinds of security measures are in place is necessary for this type of application threat modelling. A combination of manual and automated tools are available to map the application. A tool called ‘Burp’s browser’ is a manual browser that can be used. The traffic is proxied through burp automatically. By default, a live task also discovers content that can be deduced from responses, for example links and forms.
Stage 2: Analyze the attack surface
The intercepting proxy feature helps the user access and change request and response contents while in transit. It also allows the user to submit the under-monitored request/response to another appropriate Burp Suite tool, eliminating the need for copy-paste. Burp captures the proxy history through the previous phase of testing and analyses the information using ‘Target Analyzer’ and ‘Burp Scanner.’ These tools can be accessed and helps in vulnerability assessment.
Stage 3: Test for vulnerabilities
Already a range of issues could have been identified through the mapping process. By default, Burp Scanner scans all requests and responses that pass through the proxy. Burp lists any issues that it identifies under Issue activity on the Dashboard. One can also use Burp Scanner to actively audit for vulnerabilities. Scanner sends additional requests and analyses the application's traffic and behaviour to identify issues. To investigate the identified issues, multiple Burp tools can be used at once.
Some example strategies are outlined below for different types of vulnerabilities:
Various strategies can be used to approach multiple kinds of vulnerabilities.
- Input-based vulnerabilities consists of SQL Injection, Cross-site scripting, and file path traversal. To tackle the above kind of issues the features like Burp Intruder to fuzz for error messages or other exceptions and Burp Repeater to manually modify and reissue the request repeatedly and recursive grep payload type to exploit SQL injection vulnerabilities.
- Other examples could be categorised as Logic and Design Flaw. It is required to work manually to exploit these types of flaws. Multiple elements like Proxy Interception, Testing Authentication Mechanisms as well as match and replace rules or session handling rules to change the request in systematic ways and exploit the flaw.
In conclusion, penetration testing is important for meeting compliance requirements such as the PCI-DSS regulations for an annual and ongoing penetration testing. It is also important for businesses to obtain expert feedback on their existing security controls and policies as this is a practical and regulatory test that simulates a real attack and prepares the organization for handling any type of break-in. By doing consistent pen testing, businesses can obtain expert, unbiased third-party feedback on their security processes.
